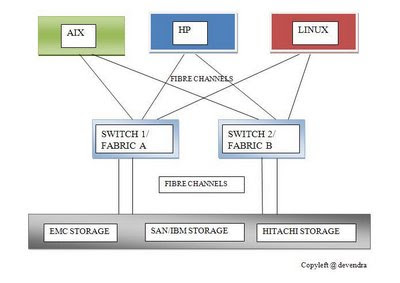
In above block diagram of
SAN system, we can see mulitple servers : AIX, HP, LINUX and may be SUN, WINDOWS etc connected to storage like EMC, SAN, HITACHI (HDS) through Fibre Channel.
In between Servers and Storage, we can see Switches also called as Fabric. This switch allows the soft zoning in between the servers and storage avoiding direct connection between Servers and Storage.
(SOFT ZONING: It is the logical connection rather than hard connection between the servers and storage )
In switch, we can activate and deactivate the created the zone in between Servers and Storage.
Wait!!! I am missing something..
To create the zoning in between the Server and the Storage, you must have
WWPN (World Wide Port Name) of either ends.
FYI there is a GUI software called as EFCM for SAN managementt.
==============================================================
Another thing to notice in above block diagram is that, each server goes to storage via two switches. Why should we use multi path?
Simple answer: For redundancy and multi path allows 2X speed of the data transfer.
Now the next question arises: What controls the multipath?
It's the multi-pathing software installed in the Servers. There are various types of mulitpating softwares. Basically there is MPIO (Multi Path I/O) which is default installed in AIX server.
There is another software: SDD (Subsystem Device Driver)
that also controls multipath.
It really depends upon your choice to use either MPIO or SDD.
Multipath can also be considered as the technique employed for Load Balancing.
=============================================================
You know there are many questions in my mind.. ;-)
Now how does the Server recognize the different vendors Storage devices?
It's real easy answer.... It's again the software/filesets.. It's like a device driver which we call Host Attachment Software/Package.
Now the bottom line concept for the SAN system to work, there are three softwares running in the servers: OS, Multipathing software and Host Attachment Software.
================================================================
Are you interested in Switch Trunking? If yes, you can go through it, ok.. Otherwise skip it.. :-)

In above block diagram it says ISL (Inter Switch Link). If the two switches are connected via ISL then this is called as Trunking. And both of the switches behave as a single switch. This increases number of possible switching. This also helps in load balancing.
(FYI: If the ports connected by ISL, the port is called as E Port. Similarly if connected by Fiber, the port is called as F Port. If nothing connected , the port is called G Port)
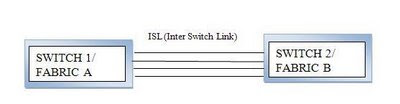
There can be more trunking lines in between two switches for efficient load balancing and efficient switching.
In SAN system, Domain ID represents Switch. Usually you will find the following notation:
97(1) which implies Switch 1 Port 97
Go and find about QLogic and Emulex...
Hey by the way, I am trying to share only my knowledge. Don't rely 100% in it.. bcoz technology is ever changing. I am trying to update my every postings.
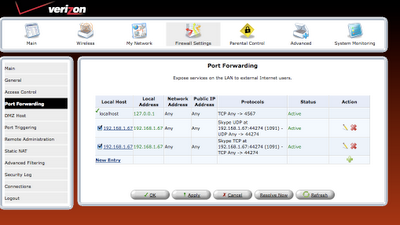
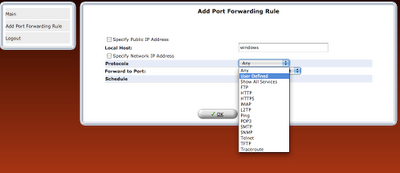
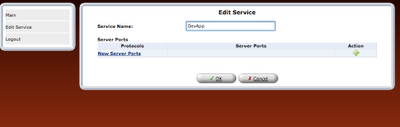
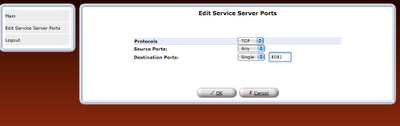
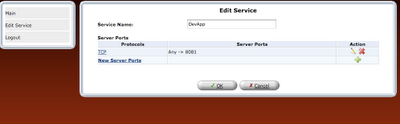
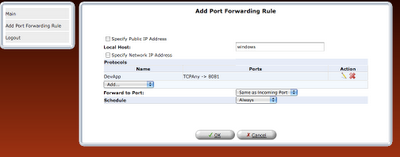
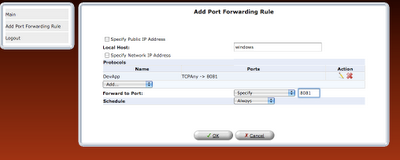

 step 8: Once the rule is defined, it should be refreshed in router or applied.
step 8: Once the rule is defined, it should be refreshed in router or applied.